Questions about out products and services
Cyber attacks continue to increase every day and are increasingly powerful, stealthy and sophisticated, randomly affecting sites, SaaS software and web applications. Companies and organizations of all sizes are therefore exposed to these cyber risks. Faced with these new threats to competitiveness, brand image and compliance, it is essential to ensure a daily offensive cyber security approach: attack your site to discover its security vulnerabilities and correct them before they are exploited by hackers. This is what HTTPCS offers.
The current technological context, especially the constant interactions and evolutions in the Cloud, make the monitoring of websites and web applications humanly impossible.
This is why HTTPCS offers the first automated cyber security tool capable of responding daily to cyber risks (web security, system security and application security, from the development chain to production).
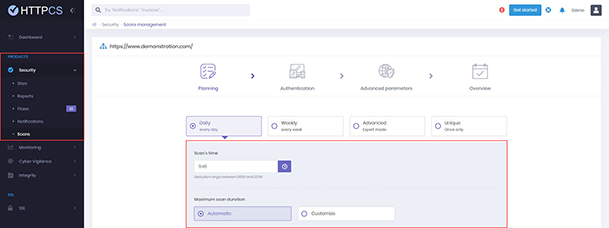
The user of the HTTPCS dashboard therefore has the possibility of scheduling his automated audits in advance and at the frequency of his choice (daily audits recommended because of his machine learning system and his daily detection of new security vulnerabilities).
- Replay the attack and understand the risks,
- Send the report to someone else,
- Apply the countermeasures proposed by HTTPCS
- the HTTPCS seal is updated after every scan
- Improve your users confidence
- Increase your conversion rate
HTTPCS is addressed to all organizations concerned with protecting websites or web applications from intrusions and web attacks.
TPE, PME, Agences web : HTTPCS is available in hosted mode (SaaS) through monthly packages without commitment adapted to their needs and constraints.
Governments of North Atlantic Treaty Organization member countries, Vital Importance Operators or Managed Services Providers: special offers are also available, notably in Appliance mode.
The GDPR requires companies collecting personal data to secure them. HTTPCS allows this data security to bring you into compliance with this aspect on the GDPR.
Indeed, by detecting security flaws on your website, and by applying patches, you protect the site against attacks and therefore the data it contains.
Encrypted data can still be stolen and decrypted. So there is a risk. However, by protecting your website from attacks, hackers will have no access to get to the data. They will then be fully protected.
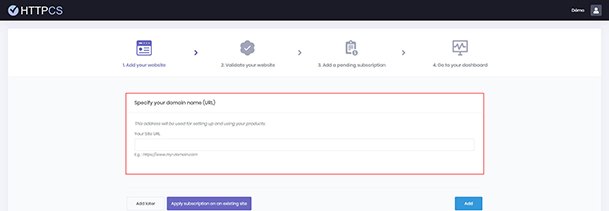
The use of HTTPCS is subject to prior verification of site ownership and legitimacy of the user to audit the application of his/her choice. This procedure can be automatic or manual:
The HTTPCS Certification Seal, whose date is updated after each "compliant" or "non-vulnerable" scan, is only issued for websites and web applications that use HTTPCS technology.
This certification ensures the reliability of the audited media, their integrity and their compliance with the ISO 27001 - ISO 27002 standards as well as the principles of the GDPR (General Data Protection Regulations set up on 25 May 2018).
This clickable certification, visible several million times a day, increases users' confidence and promotes conversion rates. It can be added to footers, legal notices or authentication pages.

To ensure optimum cyber security, HTTPCS has been designed with artificial intelligence and machine learning to detects security flaws, web applications vulnerabilities and high audience addresses in production.
All the attack simulations, even during gray box pentests (with authentication), is carried out without any interference with their integrity or availability. Users can therefore access the web application or the website during the audit.
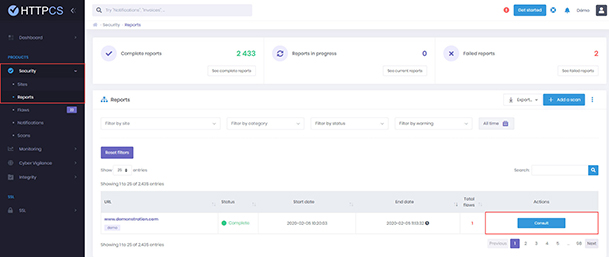
Countermeasures, adapted corrections and recommendations are detailed for each zero false positive report. The HTTPCS dashboard user, without any cyber security knowledge, is able to simply apply them without any manual reprocessing.
He can also simulate the attack with one click to understand the risks incurred. A dedicated Account Manager and online technical support are available to assist you during this implementation
HTTPCS detects all types of vulnerabilities or security flaws likely to hinder the security. availability, integrity or the compliance of your website or web application. Not restricted to malicious file propagation, defacing, data extraction, history or cookie theft , all the cyber-risks are proactively countered on a daily basis.
Rift detection is not limited to the top 10 OWASP or CVE. Every day, cyber security experts improve the robot with new hacking techniques to stay operational.
The free 14 days trial version is available with no obligations via the "FREE ACCESS" button at the top of your page or below.
This version allows to discover the ergonomics of the console, the programming of daily audits, the setting of monitoring alerts and to receive a report on the number of detected faults. Only, it will not allow you to know the details of its flaws (types and patches to apply).
Moreover, this version does not have the HTTPCS parameters to certify the level of security and reliability of the audited application. The certification seal cannot therefore be used on your website.
You can stop your HTTPCS plan any time on your client dashboard in your site parameters “automatic renewal On/Off”
Save your authentication settings to configure your Grey Box audit with our Virtual Browser. To find out more, visit the page dedicated to our vulnerability scanner.