They trust us












Cybersecurity has become a major issue for public administrations, which are increasingly exposed to computer attacks.
Public administrations store large volumes of sensitive data, such as citizens' personal information, tax data and medical records.
This data is coveted by hackers, who can use it to commit fraud, identity theft or acts of cyberterrorism.
Public administrations face a wide range of threats, including:
Ransomware attacks: hackers encrypt government data and demand a ransom to unlock it.
Data leaks: Sensitive data can be stolen and published online, which can have serious consequences for the privacy of citizens and the reputation of the administration.
Denial of Service (DDoS) attacks: Hackers can overwhelm government websites and online services with excessive traffic, making them inaccessible to citizens.
Cyberattacks can have a major impact on public administrations, including:
Disruption of public services: Cyberattacks can disrupt essential public services, such as water, electricity and transportation.
Breach of privacy: the theft of sensitive data can have serious consequences for the privacy of citizens.
Loss of trust: Cyberattacks can erode citizens' trust in public administration.
Public administrations are prime targets for cyberattacks. They collect and store large amounts of sensitive data, making them prime targets for hackers. HTTPCS by Ziwit solutions have been designed to meet the specific needs of public administrations.
HTTPCS solutions allow:
Protection of sensitive data: HTTPCS by Ziwit solutions protect sensitive data of public administrations against cyberattacks by encrypting and storing them securely.
Security of websites and online services: HTTPCS by Ziwit solutions protect government websites and online services against SQL injection attacks, denial of service (DDoS) attacks and other cyberattacks.
The benefits of HTTPCS solutions are:
Support from cybersecurity specialists: The HTTPCS by Ziwit teams support public administrations in the implementation and use of its solutions.
Training and awareness: HTTPCS by Ziwit solutions include training and awareness tools for public administration agents.
The banking and insurance sectors are prime targets for cyberattacks, given the significant amount of sensitive data they manage, including the personal and financial information of their customers. Cybersecurity has therefore become a crucial issue for the sustainability of these institutions.
Ransomware attacks: Encryption of institutional data by hackers, demanding a ransom for unlocking them.
Data leaks: Theft and online publication of sensitive data, which can cause serious damage to the privacy of customers and the reputation of institutions.
Denial of Service (DDoS) attacks: Saturating institutions' websites and online services with excessive traffic, making them inaccessible to customers.
Service Disruption: Disruption of essential banking and insurance services, such as online transactions and claims processing.
Breach of privacy: Serious consequences for customer privacy following the theft of sensitive data.
Loss of trust: Erosion of customer confidence in banking and insurance institutions.
Financial damage: Significant financial losses for institutions, through theft of funds, ransoms and repair costs.
The banking and insurance sectors face growing cybersecurity challenges. Cyberattacks can have serious consequences for these institutions.
HTTPCS by Ziwit solutions offer a complete and effective response to the specific needs of the banking and insurance sectors in terms of cybersecurity. Here are some of the benefits of using HTTPCS by Ziwit solutions:
Reinforced protection of sensitive data.
Compliance with regulatory requirements.
Improved customer trust.
Benefit from expertise and support.
HTTPCS by Ziwit solutions offer the banking and insurance sectors a comprehensive and effective solution to strengthen cybersecurity, comply with regulatory requirements and improve customer trust.
E-commerce is a booming sector, but it is also a prime target for cyberattacks. Hackers are attracted to the sensitive data that e-commerce sites collect, such as customers' personal and financial information.
SQL injection attacks: Hackers inject malicious code into web forms to steal sensitive data.
Denial of Service (DDoS) attacks: Hackers overwhelm websites with excessive traffic, making them inaccessible to customers.
Man-in-the-middle attacks: Hackers intercept communications between customers and websites to steal sensitive information.
Phishing attacks: Hackers send fraudulent emails or text messages to trick customers into disclosing their personal information.
Theft of sensitive data: Hackers can use stolen data to commit fraud, identity theft, and other crimes.
Disruption of services: DDoS attacks can prevent customers from placing orders.
Reputation damage: Cyberattacks can harm an e-commerce site’s reputation and customer trust.
Financial losses: Cyberattacks can cause significant financial losses to e-commerce sites.
The HTTPCS suite offers a complete range of tools to protect e-commerce sites against cyberattacks.
The HTTPCS Security vulnerability scanner is the most important solution for e-retailers, in fact, it allows you to:
Detect security vulnerabilities of an e-commerce site, such as XSS, SQLi and CSRF vulnerabilities.
Identify obsolete software that may contain vulnerabilities.
Provide recommendations to fix security vulnerabilities.
In addition to tools, HTTPCS also offers consulting and support services to help e-commerce sites implement an effective IT security policy.
The communications sector is on the front line of cybersecurity risks. Indeed, companies in this sector manage and distribute sensitive information, which makes them prime targets for hackers.
IT security has a major impact on the communications sector in several ways:
Communications companies collect and store large amounts of sensitive data, such as customer personal information, financial data and confidential content. IT security is essential to protect this data against theft, leaks and unauthorized access.
Trust is a crucial element for any business in the communications sector. Customers must trust that their data is protected and their communications are private. IT security helps guarantee this trust and build customer loyalty.
Cyberattacks can disrupt or even interrupt communications services, which can negatively impact a company's reputation and finances. IT security helps prevent these attacks and guarantee the continuity of services.
Cyberattacks can result in significant costs for businesses in terms of lost data, time and money. IT security helps reduce these costs by preventing attacks and minimizing their impacts.
Mise en place de solutions de sécurité informatique pour protéger les données sensibles, telles que les pares-feux, les systèmes de détection d'intrusion et le cryptage.
Formation des employés aux bonnes pratiques de sécurité informatique, telles que la création de mots de passe forts et la vigilance face aux emails et sites web suspects.
The IT sector is on the front line of cyber threats. It is therefore essential that businesses in this sector take steps to protect themselves. Here are a few tips :
Implement IT security solutions such as firewalls, intrusion detection systems and encryption.
Regularly update software and operating systems.
Regularly update software and operating systems.
Regularly update software and operating systems.
Train employees in good IT security practices such as creating strong passwords and being vigilant about suspicious emails and websites.
Establish a clear IT security policy and communicate about risks and best practices.
Raise management awareness of IT security issues.
Comprehensive protection against cyber threats: HTTPCS by Ziwit tools provide comprehensive protection against DDoS attacks, web attacks, malware and ransomware.
Rapid incident detection and response: HTTPCS by Ziwit tools enable real-time threat detection and rapid response to security incidents.
Improved security posture: Using HTTPCS by Ziwit tools helps improve the security posture of businesses and reduce the risk of cyberattacks.
By adapting to the specific needs of each business, HTTPCS by Ziwit tools can help strengthen the IT security of the IT sector and protect sensitive data from cyber threats.
In France, an operator of vital importance (OIV) is an organization that provides services or goods essential to the functioning of the nation. These organizations may include:
Energy suppliers.
Telecommunications networks.
Hospitals.
Financial institutions.
Transportation systems.
OIVs are prime targets for cyberattacks because a successful attack could have a major impact on the national economy or public safety.
In 2017, the French government adopted the Military Programming Law (LPM) which imposes a certain number of IT security obligations on OIVs, including:
Implement an IT security plan.
Perform regular security audits.
Train employees in IT security.
Notify authorities in the event of a security incident.
HTTPCS by Ziwit is a suite of cybersecurity tools that can help OIVs comply with LPM obligations and improve their level of IT security. The HTTPCS suite includes the following tools:
Risk mapping: Identifies critical assets and potential threats.
Vulnerability Assessment: Identifies vulnerabilities in computer systems.
Incident management: Helps respond to security incidents.
Training and Awareness: Helps train employees on IT security.
The HTTPCS suite is Cyber Essentials certified, meaning it meets the UK government's IT security requirements.
Improved IT security: Identify and correct vulnerabilities in their IT systems.
Compliance with the LPM: Comply with the obligations of the LPM in terms of IT security.
Reduction of the risk of attack: Reduce the risk of being victims of a cyber attack.
Better Incident Response: Respond to security incidents more effectively.
The healthcare sector has become a prime target for cybercriminals. In 2023, attacks have increased exponentially, with serious consequences for patients, healthcare professionals and healthcare systems in general.
Sensitive and valuable data: Medical records contain confidential and sensitive information, making them a prime target for hackers looking to resell or exploit them for malicious purposes.
Often old and poorly secured systems: Hospitals and clinics often use aging IT systems that are not up to date with security, making them more vulnerable to attacks.
Lack of risk awareness: Healthcare personnel are not always sufficiently aware of cybersecurity risks, which can make the task of hackers easier.
Disruption of healthcare services: Attacks can paralyze hospital IT systems, which can delay or cancel surgeries, consultations and other critical services.
Medical data theft: Hackers can steal medical records, which can put patients' privacy at risk and put them at risk of health insurance fraud.
Reputational damage: A cyberattack can tarnish the reputation of a healthcare organization and harm patient trust.
Significant financial costs: Cyberattacks can be costly to healthcare organizations due to the cost of repairing IT systems, loss of data and potential litigation.
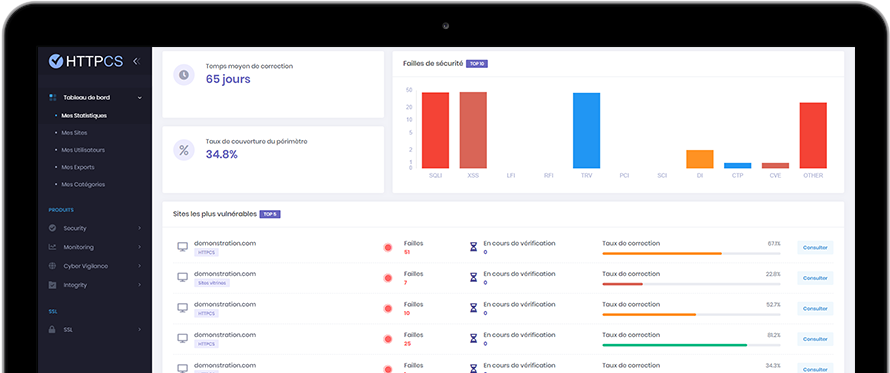
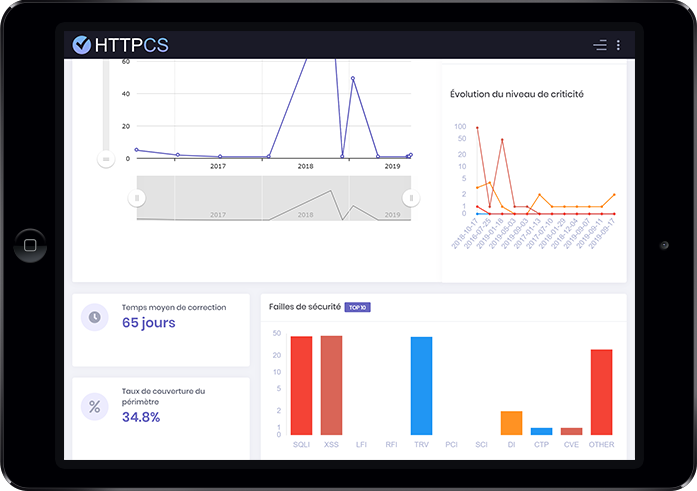
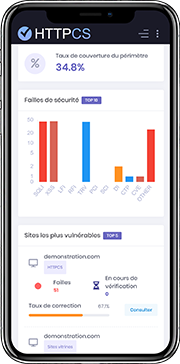
The HTTPCS Security Vulnerability Scanner is a powerful tool that can help healthcare organizations identify and fix security vulnerabilities in their websites and web applications. It is a comprehensive tool that offers a number of features:
Detection of OWASP and CVE vulnerabilities: The scanner can detect a wide range of known vulnerabilities, including those listed in the OWASP Top 10 and CVE database.
Dynamic content analysis: The scanner uses a real browser to analyze the dynamic content of websites and web applications, allowing it to detect vulnerabilities that might be missed by other scanners.
Detailed Reports: The scanner generates detailed reports that identify discovered vulnerabilities and provide recommendations to fix them.
The tourism sector is increasingly dependent on digital technologies. Websites, mobile applications and online reservation systems have become essential tools for tourism businesses to attract and retain customers.
However, with this growing reliance on digital technologies comes an increased risk of cyberattacks. Hackers can target tourism businesses to steal sensitive data, such as customers' credit card information or travelers' personal data.
Cyberattacks can have a devastating impact on tourism businesses. They can lead to significant financial losses, loss of reputation and reduced customer trust.
Phishing Attacks: Phishing attacks are fraudulent emails or text messages that trick recipients into revealing their personal information.
Ransomware attacks: Ransomware attacks are attacks that block access to company data and demand payment of a ransom to unlock it.
SQL Injection Attacks: SQL injection attacks are attacks that allow hackers to modify or delete data in a database.
Cross-site scripting attacks: Cross-site scripting attacks are attacks that allow hackers to inject malicious code into a website, which can infect visitors' computers.
Vulnerability Scanning: The HTTPCS Security tool scans tourism company websites and applications to identify vulnerabilities that could be exploited by hackers.
Protection against SQL injection attacks: The HTTPCS Security tool protects websites and applications from SQL injection attacks, which can allow hackers to steal data or modify sensitive information.
Protection against cross-site scripting attacks: The HTTPCS Security tool protects websites and applications from cross-site scripting attacks, which can allow hackers to inject malicious code into web pages and infect visitors' computers.
Threat Monitoring: The HTTPCS Security tool continuously monitors tourism business websites and applications for signs of attack.
Reports and Alerts: The HTTPCS Security tool generates reports and alerts to inform tourism businesses of potential threats and security incidents.
The transportation and logistics sectors are prime targets for cybercriminals. This is because they are responsible for managing large amounts of sensitive data, such as customer information, transportation routes and cargo. Additionally, IT systems in these sectors are often critical to the operation of national and international infrastructures.
Ransomware attacks: Ransomware is malware that blocks access to company data and demands payment of a ransom to unlock it. In 2021, the transportation sector was the second most targeted sector by ransomware.
SQL injection attacks: SQL injection attacks allow hackers to steal data or modify sensitive information in databases.
Denial of Service (DoS) Attacks: Denial of service attacks aim to make websites and applications unavailable by overloading them with traffic.
Cyber espionage: Cyber espionage aims to steal sensitive information, such as trade secrets or customer information.
Data leaks: Data leaks can be caused by human errors, malware or intrusions into computer systems.
Hacking of navigation systems: Navigation systems of aircraft and ships can be hacked, which can endanger the safety of passengers and cargo.
The HTTPCS Security scanner is an IT security tool specifically designed for the needs of the transportation and logistics sectors. It helps identify vulnerabilities in websites and web applications in these sectors, and patch them to protect them against cyberattacks.
The HTTPCS Security scanner is a comprehensive tool that offers several features:
Vulnerability Scanning: The HTTPCS Security scanner scans websites and web applications to identify vulnerabilities that could be exploited by hackers.
Protection against SQL injection attacks: The HTTPCS Security scanner protects websites and web applications against SQL injection attacks, which can allow hackers to steal data or modify sensitive information.
Protection against cross-site scripting attacks: The HTTPCS Security scanner protects websites and web applications against cross-site scripting attacks, which can allow hackers to inject malicious code into web pages and 'infect visitors' computers.
Threat Monitoring: The HTTPCS Security scanner continuously monitors websites and web applications for signs of attack.
Reports and Alerts: The HTTPCS Security scanner generates reports and alerts to inform businesses in the transportation and logistics industries of potential threats and security incidents.