Protect your data to be GDPR compliant
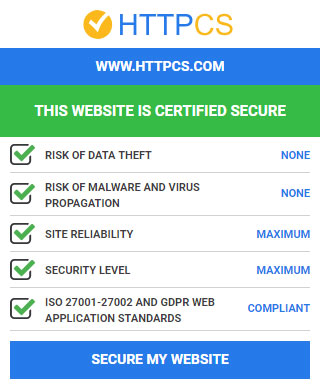
Here the European Data Protection Regulation is, and it is necessary for you to comply with it! By offering a secure and sustainable solution to secure your websites and web applications, our system, Security by HTTPCS, helps you in this process. Thanks to our offensive cybersecurity solution, you are actors of the protection of your data as the GDPR obliged to.
Concerning data security, Ziwit, European leader in IT security, gives you the necessary tools to pass with serenity the GDPR step.