How to make a local file inclusion?
Include is a very easy to use function but which can be dangerous… Indeed, malicious people can inject a file other than the desired one. This is called local file inclusion or LFI which is a web security vulnerability. HTTPCS shows you in this article that it is necessary to protect yourself against such piracy.
Most php websites use the’include’ function which includes and executes the file passed as parameter.
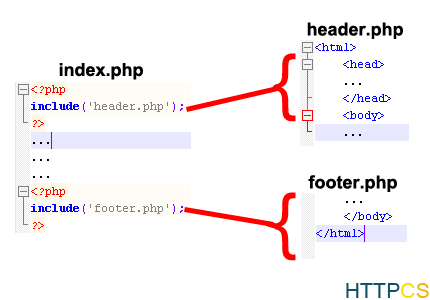
Include injects the code (html or php) and executes it at the exact location where the function is located.
We can thus change the header of a website of several thousand pages from a single file (header.php) which will be included later in the other pages.
Whereas with a static html site you have to open page by page to modify it.
This very easy to use function is sometimes dangerous.
Indeed some developers use it with unfiltered input parameters.
‘Include’ dangers:
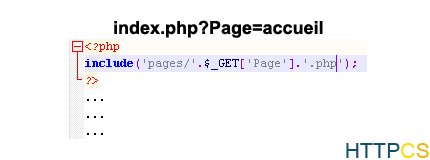
The developer provides links with a ‘Page’ parameter that concatenates with the value’pages/’ at the beginning, and ‘.php’ at the end.
The’Pages’ folder contains php files that our developer wants to include according to the pages of his site.
In our example’index.php ?Page=home’ will include the file’pages/accueil.php’ at the beginning of the page.
Nevertheless a malicious person can very well change the value of the parameter’Page’ to ../index’, the result will be different and the page that will be included at the beginning will be’page/../index.php’.
It is therefore possible to include other files and to move up the’pages’ folder.
This is what is called the local file inclusion or LFI which is a web security vulnerability consisting in injecting a file other than the desired one.
It is then possible for us to upload folders and include any file, not just’.php’ files.
In order to include files with other extensions, it is enough to comment the continuation of the injection with”%00′ for example:
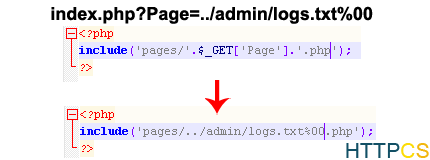
A malicious person can therefore write to the php command logs, and then include this file in order to execute it.
The local file inclusion is extremely critical.
Try for free our vulnerability scanner
