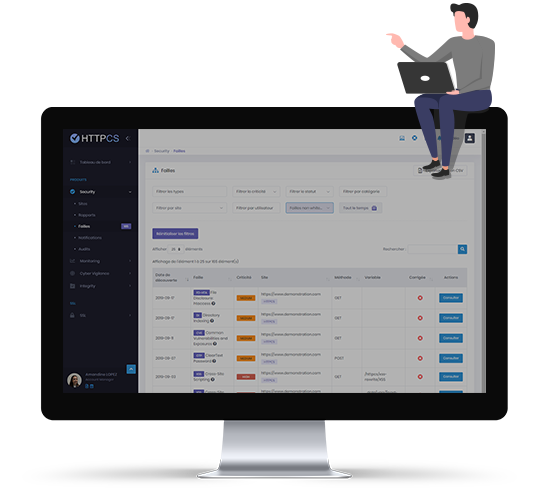
Detect security issues on your website and web application
Put yourself in a hacker's shoes! Without technical expertise, run automated security audits to detect vulnerabilities on your website or web application. With detailed reports, you'll know exactly what security issues hackers can exploit, their criticality levels and how to fix them. You can even replay the attacks to understand the risks involved. HTTPCS Security puts Machine Learning at the service of your cyber security to protect your site against hacking and data leaks.
100% Mapping
100% vulnerability scanning mapping means that the tool has scanned all pages and all possible actions of a website or web application, including those using dynamic content (scrolling, buttons, contact forms, modals, etc.). The aim is to identify all entry points and possible paths for exploiting a security vulnerability. Indeed, modern websites increasingly use dynamic technologies that can generate pages and features not accessible via static links.
HTTPCS headless technology allows the robot to make full user interactions on page elements. (hover and click mouse, scrolling and filling up fields & forms). The actions are memorized to set up scenarios allowing the discovery of menus, pop-up and multi-step forms.
To achieve 100% mapping, our vulnerability scanner uses various techniques, including:
- Crawling: exploring the website by following hyperlinks and analyzing the content of pages.
- Source code analysis: identifying entry points and possible paths in the website's source code.
- Fuzzing: sending random requests to discover hidden pages and features.
« Zero false positive » guaranteed
From the HTTPCS console, get access to all security issues detected by our vulnerability scanner. HTTPCS guarantees « zero false positive » : any detected vulnerability corresponds to a real threat that could be exploited by hackers.
As proof, HTTPCS Security identifies and simulates the security flaw without affecting your website or web application and gives you the opportunity to replay the attack.
No more wasting time going through long reports, trying to figure out which flaws are real or not: our technology does it for you and indicates for each threat its CVSS 3.0 severity score as well as possible counter-measures for you to fix this vulnerability
Prioritize your actions with our SECURITY Rating
Our Security Rating allows you to have a synthetic view of the vulnerability level of a website.
It is calculated by taking into account all the security data (security flaws, configuration warnings and CVE of detected technologies)
Thanks to this rating, you can save time and prioritize easily your efforts in remediating on your most strategic sites.
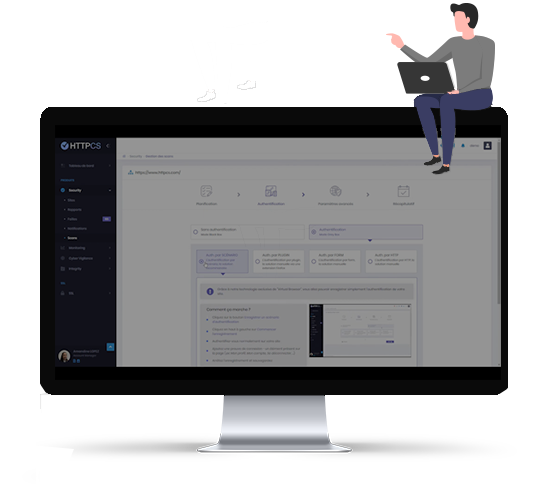
Scanning with authentication (or gray box testing) is a penetration testing method that allows you to simulate an attack carried out by a hacker with limited access to the target system.
In the case of the HTTPCS Security Vulnerability Scanner, this means that the scanner can be used to scan websites and web applications that require authentication to access them.
The HTTPCS Security Vulnerability Scanner uses a proprietary technology called Virtual Browser to record a website's authentication process. This allows the scanner to leverage authentication information to scan the website in depth, including password-protected areas.
Scanning with HTTPCS Security authentication offers several advantages, including:
- A more comprehensive scan: The scanner can scan the entire website, including password-protected areas, uncovering security vulnerabilities that might otherwise go unnoticed.
- Better understanding of risks: The scanner can provide information on how hackers could exploit discovered security vulnerabilities, allowing companies to better prioritize their remediation efforts.
- Reduced costs: By identifying security vulnerabilities early in development, companies can avoid higher remediation costs later.
HTTPCS Security's daily automated audits are an effective way to keep your websites and web applications secure. By performing regular scans, you can identify security vulnerabilities as soon as they appear, allowing you to quickly patch them and reduce your risk of cyberattacks.
Easy to set up and to use, the HTTCS Security interface allows you to schedule daily audits to protect your website 365 days a year.
With just a few clicks, configure the desired audit (using default or advanced mode, according to your needs) and receive daily reports for optimal protection throughout the year.
Web Vulnerability scanner with Machine Learning
The HTTPCS Security Machine Learning Web Vulnerability Scanner is a powerful tool that uses artificial intelligence to identify security vulnerabilities on your websites and web applications.
Unlike traditional scanners that rely on pre-existing rules and signatures, the HTTPCS Security scanner uses a scalable machine learning model to scan your website and identify security vulnerabilities, even if they are new or unknown.
At each scan, the robot crawls through your site or web app testing a variety of attack scenarios and learning from each scan before defining new attack strategies in order to identify and confirm new vulnerabilities.
By running HTTPCS Security every day, new vulnerabilities might therefore be detected from new strategies, from changes to your information system and from newly identified cyber threats. Far more thorough than a « one shot » audit, our robot replicates the behaviour of hackers looking for any vulnerability in your system.
The HTTPCS Certification Seal is a visible way to demonstrate that your website or web application has been audited by HTTPCS Security and is free from critical security vulnerabilities. The seal is a sign of trust for your visitors, and it can help you increase your conversion rate and improve your reputation.
To obtain the HTTPCS certification seal, you must first have your website or web application scanned by the HTTPCS Security vulnerability scanner. This scanner scans your website for known security vulnerabilities, and it generates a detailed report that describes the vulnerabilities identified and their severity level.
Once you have fixed all critical security vulnerabilities, you can apply for the HTTPCS certification seal. HTTPCS Security will then perform a final audit of your website or web application to ensure it complies with its strict security standards.


They trust the HTTPCS Security Vulnerability Scanner













Ziwit (HTTPCS) has the VISA
The PASSI qualification is a security VISA issued by the ANSSI (National Agency for the Security of Information Systems). This certificate issued by ANSSI bears witness to our skills and expertise as auditors, but also to the attention we pay to protecting the integrity of the confidential information to which we may have access during our services to our customers.

Ziwit (HTTPCS) holds the label
Ziwit (HTTPCS) expert in digital security, guarantees technical expertise as well as quality advice to prevent acts of cyber-surveillance and secure your IT installations and your websites.
As an ExpertCyber certified service provider, Ziwit (HTTPCS) is committed to respecting its charter of commitments.
Ziwit (HTTPCS) holds the label
The France Cybersecurity label offers the guarantee that the labeled products, solutions and services are designed, developed and operated in France, by a dynamic and innovative industrial sector recognized by the market. It is therefore a mark of excellence for companies.

Ziwit (HTTPCS) holds the label Qualiopi
QUALIOPI is the unique quality certification mark for training organizations. It has been mandatory since January 1, 2022. ZIWIT fully complies with the 32 new indicators in the national quality reference framework, organized around 7 quality criteria. Our training courses can therefore be referenced by accredited organizations and are eligible for funding.

Ziwit (HTTPCS) is part of the national systemcyber malicious
mission is to support victims of cyberattacks through its cybersecurity solutions and tools.
As a service provider listed on the french government platform Cyber Malicious, Ziwit (HTTPCS) is committed to respecting its charter of commitments.
Our C)PTE certified cybersecurity experts (CERTIFIED Penetration Testing Engineer)
Developed on the basis of the US Force One methodology, and accredited by both the NSA and the FBI, this certification allows us to explore all the existing technical and non-technical means of accessing an information system in an illicit way. Our pentesters are trained in the art of ethical hacking and the latest techniques in penetration testing, with the aim of recognizing each key element: Information gathering, scanning, enumeration, exploitation and reporting.

Our CEH certified cybersecurity experts (Certified Ethical Hacker)
Our pentesters are experienced in vulnerability research. They have the internationally recognized CEH certification to guarantee you a qualified and ethical technical auditor.

Ziwit is certified OSCP (Offensive Security Certified Professional)
OSCP is an ethical hacking certification offered by Offensive Security (or OffSec) that teaches penetration testing methodologies and the use of the tools included with the Kali Linux distribution. The OSCP is a hands-on penetration testing certification, requiring holders to successfully attack and penetrate various live machines in a safe lab environment.

Ziwit is certified OSCP (Practical Network Penetration Tester)
Delivered by TCM Security, the PNPT certification is a unique ethical hacking exam that evaluates a pentester's ability to perform a professional level network penetration test and its potential to perform open source research (OSINT) to gather information on how to properly attack that network. Our pentesters know how to make the most of their Active Directory exploitation skills to perform A/V and egress bypasses, lateral and vertical network movements, and ultimately compromise the domain controller under investigation.

Ziwit (HTTPCS) holds the Cyber Essentials certification
Cyber Essentials is a certification supported by the British government (United Kingdom) to help organizations ensure operational security against cyber attacks.

Ziwit holds the IASME GDPR certification
Issued by the IASME consortium and supported by the UK Government, "IASME GDPR" reinforces Cyber Essential by validating Ziwit's GDPR skills, and its ability to comply with its requirements. IASME GDPR certification is proof that ZIWIT has taken enhanced measures to protect your business and your data from cyber-attacks on the Internet.

Ziwit (HTTPCS) holds the Cybersecurity Made In Europe certification
The "Cybersecurity made in Europe" certification is designed to promote European cybersecurity companies and increase their visibility on the European and global market. The certification raises awareness of the strategic value of cybersecurity companies originating in Europe and developing their activity on the basis of European values of trust.

Ziwit (HTTPCS) is a member (Alliance for digital trust)
ACN is a group of companies that award services, solutions and technologies that mitigate risk and therefore increase trust.

Ziwit (HTTPCS) is an associated memberCampus Cyber
Campus Cyber will be a French hub of cybersecurity by 2022 that will bring together the main national and international players in the field.
Small business < 50 Employees
$ 97 / site
Monthly Billed
free trialYou have already tried a product from this category
or
Full
Managed Vulnerability Scanner
Outsource your IT security using our services and benefit from the expertise of cybersecurity experts to detect and correct your vulnerabilities!
Contact usBlack box scan: simulates a hacker with no prior knowledge of your system (no authentication). Grey Box scan: for a much deeper scan, give the robot login credentials to identify a full range of vulnerabilities.
WEB/APPLICATION AND SYSTEM PERIMETER
Scan of web servers, websites or web applications through headless technology: protection of extranets, intranets, SaaS applications, e-commerce websites and institutional sites for an optimal protection of your client/server addresses.
The HTTPCS robot detects an extensive range of vulnerabilities, not limited to the Top 10 OWASP and CVE. The robot knowledge base is supplemented every day by our cyber expert team in order to take into account new cyber threats in real time.
EXTERNAL NETWORK CRAWL
List of open ports, exposed services Fingerprint (FPT, SSH, Telnet, SMTP, SSL...), CVE via exploits of services (Ex port 445 SMB Wanna Crypt), SSL certificates (Chain & Validity), Reverse DNS.
NO INSTALLATION REQUIRED
There is no need to download and deploy any software to your servers. Our solution is SAAS based so you will be able to access it from a web platform by simply logging in to your secure console at httpcs.com.
Each HTTPCS subscription gives you access to a dedicated Account Manager who will be there for you, right from your first steps with HTTPCS Security and at any time you need some information or advice.
Frequently Asked Questions
How to protect a website or web application?
The current technological context, especially the constant interactions and evolutions in the Cloud, make the monitoring of websites and web applications humanly impossible. This is why HTTPCS offers the first automated cyber security tool capable of responding daily to cyber risks (web security, system security and application security, from the development chain to production).
How to fix a vulnerability detected by an HTTPCS audit?
Countermeasures, adequate corrections and recommendations are detailed for each vulnerability listed in each report. HTTPCS dashboard users, with limited cyber security knowledge, can simply implement these corrections which will automatically be detected by the robot and marked as such.
Who is the HTTPCS Security vulnerability scanner designed for?
If you are a VSE, an SME, a web agency, an ESN, a government or an OIV, you have the responsibility to protect the data of your customers and your users.
HTTPCS is a comprehensive and flexible solution that gives you optimal protection against cyberattacks, including: intrusions, web attacks, ransomware, phishing, SQL injections, XSS attacks and much more.
HTTPCS adapts to your needs and your budget. You can choose from a variety of monthly plans without commitment, or opt for a tailor-made offer in SaaS or Appliance.
How is a vulnerability scanner crucial for the security of a website or web application?
The cyber threat landscape is constantly evolving. Cyberattacks are increasingly frequent, sophisticated and can affect any company, regardless of its size or sector of activity. SaaS software has become a prime target for cybercriminals because it often centralizes sensitive data.
The consequences of a cyberattack can be devastating for a company: Loss of sensitive data, Business interruption, Damage to brand image, Financial or legal sanctions. Faced with these risks, it is essential for companies to put in place adequate security measures.
A vulnerability scanner is a valuable tool for identifying and fixing security vulnerabilities that could be exploited by hackers.
Is it possible to audit a website (URL, IP, address) that does not belong to me?
The use of HTTPCS is subject to strict access control to ensure the security and confidentiality of your data. Only the legitimate owner or manager of the website can initiate a check and launch an audit. Three simple and secure options are available to perform this verification:
- Telephone verification: A telephone exchange with our team allows us to confirm your identity and your link with the website to be audited,
- The Transfer of a cookie file: The posting of a specific file on your website demonstrates your access and control over it,
- The Signed written attestation: For consultants, web agencies or MSPs, an official signed attestation can be provided to validate your authorization to audit the website.
Is it possible to audit a website in production or with a large audience without disrupting its operation and its users?
Protect your production or high audience website without taking it offline. The HTTPCS Security Vulnerability Scanner is a cybersecurity solution designed to detect vulnerabilities in your website without disrupting its functionality or your users' experience.
Even complex attack simulations, including gray box pentests with authentication, are carried out securely. Our innovative technology guarantees the integrity and availability of your website during the audit, allowing Internet users to access it without interruption.
With HTTPCS Security, you benefit from a complete and accurate audit of your website, without any negative impact on its activity.
What does the HTTPCS report contain? What are the vulnerability types detected?
HTTPCS is the complete and proactive cybersecurity solution you need to protect yourself against all threats, including :
- The spread of malicious files (malware, ransomware, etc.),
- Defacement of your website,
- Vacuuming of your database,
- Theft of browsing history or cookies,
- SQL injection attacks,
- XSS attacks,
- Phishing, etc.
HTTPCS goes beyond traditional security solutions, among these advantages there is :
- The Vulnerability detection not limited to top 10 OWASP or CVE,
- Daily updates from cybersecurity experts,
- Protection against new hacking techniques, including zero-day attacks,
- Security scanner Built-in Vulnerabilities,
- Detailed Security Risk Reporting,
- Real-Time Threat Tracking and Analysis,
- 24/7 Technical Support.
How does the proposed 14-day free trial work?
Test our vulnerability scanner without obligation and get an overview of the security of your website.
The free trial allows you to:
- Access the HTTPCS console and discover its features.
- Obtain a report on the number of vulnerabilities detected on your website.
- Identify the most critical types of flaws.
The details of the flaws and the fixes to be applied will not be available in the free version.
The HTTPCS certification seal will not be usable during the free trial.
To obtain complete protection and benefit from all the features of HTTPS, it is necessary to subscribe to a paid subscription.
Start your free trial today and find out how HTTPCS can protect your website!
Click the "TEST HTTPCS" button to register.